Ransomware attackers aren’t hackers, they’re operators.
Know this and block 90% of their attacks.
If your picture of a hacker is someone in a dark room typing genius code from scratch, you’re about ten years out of date.
Ransomware isn’t a story about lone coders anymore. It’s a business.
Think of it like Ransomware as a Service. You rent the malware. You follow the guide. You split the profit.
In today’s insight, I’m walking through how BlackCat (ALPHV) shaped this whole model, why it still matters even after the takedown, and the steps you can take right now to stop most RaaS attacks before they spread.
From this guided insight, you will:
👉 Understand how RaaS really works
👉 Learn what indicators actually matter
👉 See how to block the tools attackers rely on daily
Know your attackers’ tools, defend with precision.
The Myth vs The Model
Here’s the truth: ransomware today isn’t driven by genius. It’s driven by structure.
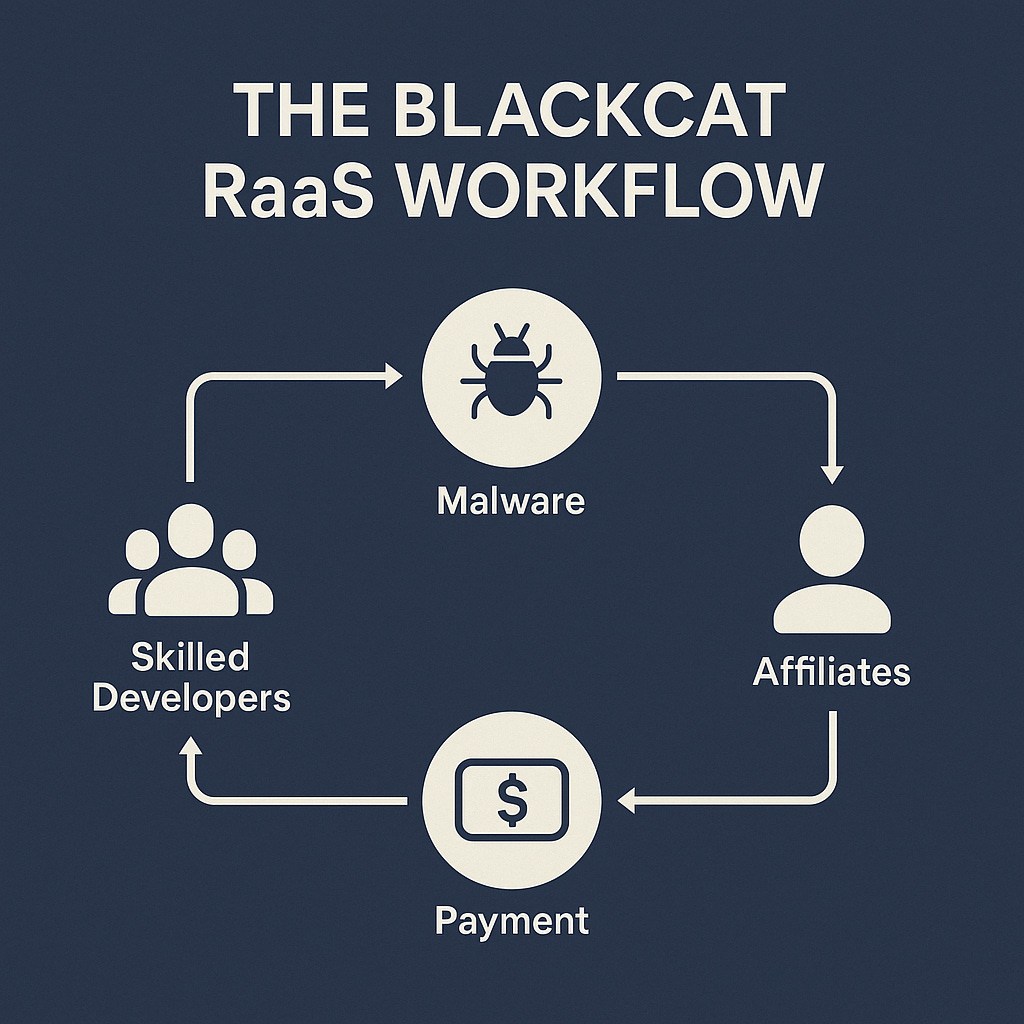
The days of lone hackers are mostly gone. In their place, you’ve got a commercialised underground economy with developers, affiliates and profit splits.
It’s sold as RaaS, Ransomware as a Service. I sometimes call it Rent a Service because that’s basically what it is.
You don’t need to write code anymore. You use what’s already out there. You rent it, repurpose it or tweak existing malware, then run the job and split the profit.
Over time, the market professionalised
A small group of skilled developers started building solid ransomware toolkits with admin panels, payment systems and clear instructions.
They offered these platforms to operators on private channels. Sometimes rented, sometimes sold, copied from leaked code.
Affiliates buy access, pick their targets and run the attacks.
Developers look after the platform, handle payments and take their cut.
That’s how a few coders can fuel hundreds of global breaches. And BlackCat (ALPHV) shows this better than anyone.
What Is BlackCat (ALPHV)?
Why this matters: it’s the playbook for professional ransomware operations. It’s modular, runs on different systems, and feels a lot like commercial software.
BlackCat, also called ALPHV or Noberus, showed up in late 2021.
It’s written in Rust, one of my favourite languages. I’ve got a soft spot for Go and Elixir, too.
Rust is fast, memory safe and tough to reverse engineer, which makes it great for staying hidden.
Unlike older strains, BlackCat runs on Windows, Linux and VMware ESXi. So it hits both cloud and on-premises systems.
The code is clean, the logic is tight, and the whole thing feels like it was built to make money rather than cause random chaos.
How BlackCat Works
Why this matters: Knowing the flow helps defenders break it before anything gets encrypted.
BlackCat runs on the Ransomware as a Service model. Developers keep the platform running, and affiliates carry out the intrusions.
Here’s the attack flow:
Initial Access: through phishing, stolen RDP credentials or exploited weaknesses like ProxyShell, Log4j or ESXi flaws.
Lateral Movement: using tools like Cobalt Strike, AnyDesk or PsExec to move through the network, gain higher access and shut down security controls.
Data Exfiltration: before any encryption starts, sensitive data is taken for double extortion.
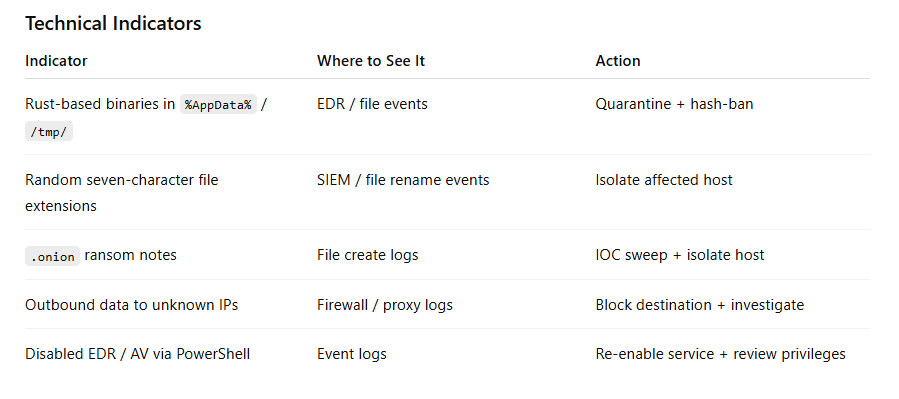
Encryption: files are locked with AES 256 and ChaCha20. A random seven-character extension is added, and system files are skipped so the device can still boot.
Ransom Demand: a note drops with a dot onion link for negotiation. Payment is usually Bitcoin or Monero.
Affiliates keep most of the profit. Developers take a smaller platform cut.
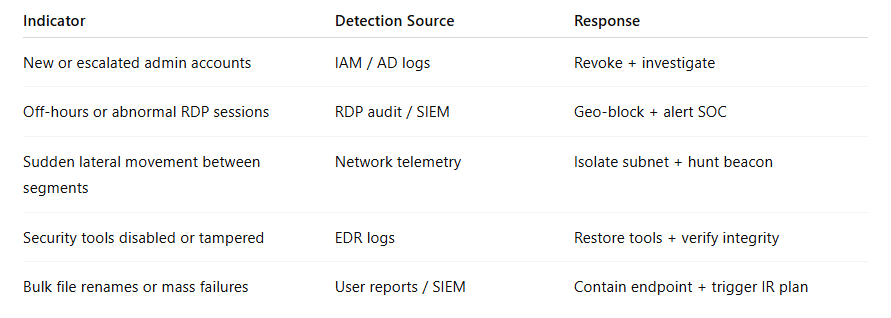
Attack Indicators
Why this matters: Early detection often decides whether an event becomes an incident.
Behavioural Indicators
What to Do About It
Why this matters: precision beats panic. These actions close the paths BlackCat-style operators depend on.
Multi Factor Authentication (Platform / SecOps)
Use hardware tokens or certificate-based MFA. Skip SMS codes.
Verify: check a sample of high-privilege logins each week.
Patch Vulnerabilities (IT Ops)
Focus on Exchange issues like ProxyShell and ProxyLogon, Log4j, VMware ESXi, Fortinet and SonicWall.
Verify: keep monthly reports that track each weakness through to patch.
Network Segmentation (Network / SecOps)
Follow Zero Trust ideas. Keep critical systems isolated and block sideways movement by default.
Verify: run quarterly drills that test sideways movement.
Remote Access Controls (IT Ops)
Allow only approved remote tools. Block everything else through Group Policy.
Verify: review a weekly software inventory diff.
Backups (IT Ops)
Use the three two one rule. Three copies, two types of media, one kept offline.
Verify: run a monthly restore test and write down the result.
EDR and Threat Hunting (SecOps)
Watch for Rust payloads, Cobalt Strike traffic, mass file locks and strange data staging.
Verify: produce weekly hunt reports with IOC checks.
Identity and Privilege Controls (SecOps / HR)
Keep access tight, rotate admin accounts and use Just in Time access.
Verify: review all raised access each month.
Insider Risk Monitoring (SecOps / HR)
Watch for odd admin behaviour, sudden privilege jumps and unusual access patterns.
Verify: send a behavioural report and raise anything that stands out.
Quick Wins (5 Minutes)
Why this matters: small changes stack up fast. These actions close the gaps that attackers use every day.
Most attackers don’t write code on the fly. They use normal admin tools, the same ones your IT team trusts.
Cut off their access to these, and you slow them down fast.
🖥️ RDP
A common path in.
Turn off external RDP.
If you really need it, put it behind a VPN or a jump host.
Use hardware MFA like a YubiKey.
Watch for failed logins and odd locations.
🎯 Cobalt Strike
Common in cracked form.
Pull in CISA IOCs for active command paths.
Use community SSL and TLS intel feeds like abuse.ch SSLBL.
Let your EDR or IDS watch for Beacon patterns because domain blocks alone are never enough.
🧰 AnyDesk and TeamViewer
Easy backdoor tools for intruders.
Keep only the approved ones.
Remove anything unapproved through Group Policy.
Let only admins install remote tools.
🔑 Mimikatz
Used to pull credentials.
Turn on LSASS protection with RunAsPPL.
Make sure WDigest is off. It is off by default on recent Windows builds. If you run older ones, apply KB2871997, then turn it off.
Watch for dumping behaviour in your EDR.
Rotate high-privilege passwords on a regular schedule.
⚡ PowerShell and PsExec
Built-in tools are often used in attacks.
Limit PowerShell to signed or admin-approved scripts through WDAC or AppLocker.
Log Event IDs 4104 and 4688, and watch 5861 for WMI persistence.
Limit PsExec for non-admins and push all logs to your SIEM.
Outcome: you’ve now blocked around ninety percent of real-world ransomware tradecraft, including BlackCat.
Final Thought
BlackCat isn’t just another ransomware strain. It’s a template for how modern cybercrime grows and keeps itself going.
Assume breach. Verify everything. Patch fast. Segment deep. Back up smart.
Know the tools attackers use and defend with precision.